Networking Commands and Troubleshooting

Networking Commands for Windows and Linux
Networking commands are essential for diagnosing, troubleshooting, and managing network-related issues on both Windows and Linux systems. Here, we’ll explore some commonly used networking commands and their usage on both platforms, as well as troubleshooting steps to resolve common network problems.
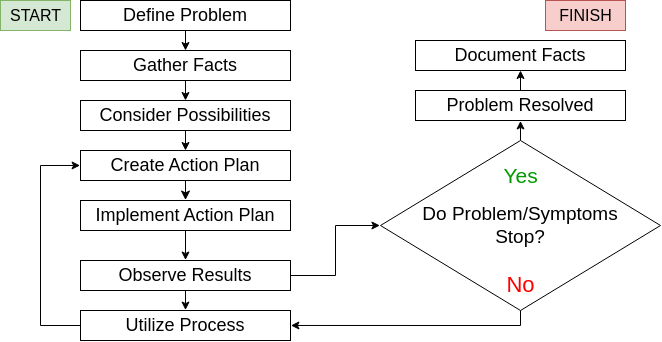
Network Troubleshooting Steps
- Check Hardware
- Use ipconfig (or ifconfig)
- Use ping and tracert (traceroute)
- Perform DNS check
- Check for Virus/Malware
- Review Database Logs
- Contact ISP (Internet Service Provider)
Additional Steps:
- Check physical connections: Ensure all cables are securely plugged in and not damaged.
- Restart networking equipment: Rebooting routers, switches, and modems can often resolve temporary network issues.
- Verify firewall and security settings: Incorrect firewall configurations can block network traffic and cause connectivity problems.
- Check for software updates: Ensuring operating systems and network devices have the latest updates can address known issues and vulnerabilities.
Network Troubleshooting Diagram
 Windows Networking Commands
Windows Networking Commands
IPCONFIG
IPCONFIG is used to display the current TCP/IP network configuration values assigned to network interfaces on Windows systems.
ipconfigPING
PING is used to test the reachability of a host on a network and measure the round-trip time for packets sent from the local system to the target host.
ping <hostname or IP address>NETSTAT
NETSTAT displays active network connections, routing tables, interface statistics, masquerade connections, and multicast memberships.
netstatnetstatRead more about netstat and netstat -ano commands
netstatNETSTAT displays active network connections, routing tables, interface statistics, masquerade connections, and multicast memberships.
When you run netstat without any options, it provides a list of active connections along with the corresponding protocols (TCP/UDP), local and foreign addresses, and their status.
Example output of netstat:
| Protocol | Local Address | Foreign Address | State | PID |
|---|---|---|---|---|
| TCP | 0.0.0.0:135 | 0.0.0.0:0 | LISTENING | 1234 |
| TCP | 0.0.0.0:445 | 0.0.0.0:0 | LISTENING | 5678 |
| TCP | 0.0.0.0:3389 | 0.0.0.0:0 | LISTENING | 9012 |
| … | … | … | … | … |
In this table:
Protocol: Protocol used by the connection (e.g., TCP).Local Address: Local IP address and port.Foreign Address: Remote IP address and port.State: Connection state (e.g., LISTENING, ESTABLISHED).PID: Process ID of the application or service associated with the connection.
netstat -anoNow, let’s look at the netstat -ano command and explain its components:
a: This option displays all connections and listening ports.n: This option displays addresses and port numbers in numerical form, rather than resolving hostnames and service names.o: This option displays the owning process ID associated with each connection.
Example output of netstat -ano:
| Protocol | Local Address | Foreign Address | State | PID |
|---|---|---|---|---|
| TCP | 0.0.0.0:135 | 0.0.0.0:0 | LISTENING | 1234 |
| TCP | 0.0.0.0:445 | 0.0.0.0:0 | LISTENING | 5678 |
| TCP | 0.0.0.0:3389 | 0.0.0.0:0 | LISTENING | 9012 |
| … | … | … | … | … |
In this table:
Protocol: Protocol used by the connection (e.g., TCP).Local Address: Local IP address and port.Foreign Address: Remote IP address and port.State: Connection state (e.g., LISTENING, ESTABLISHED).PID: Process ID of the application or service associated with the connection.
This information can be useful for identifying which processes are using network resources, troubleshooting network issues, or identifying potentially unwanted or malicious connections.
Remember, on Windows systems, the PID can be cross-referenced with the Task Manager to identify the specific process that’s using a particular network connection.
netstat -ano | findstr "LISTENING"Another useful way to filter the netstat -ano output is by using the findstr command to specifically look for listening ports. This can help you quickly identify which processes are listening for incoming connections.
The findstr "LISTENING" command filters the output to show only the connections that are in the LISTENING state.
Example output after filtering:
| Protocol | Local Address | Foreign Address | State | PID |
|---|---|---|---|---|
| TCP | 0.0.0.0:135 | 0.0.0.0:0 | LISTENING | 1234 |
| TCP | 0.0.0.0:445 | 0.0.0.0:0 | LISTENING | 5678 |
| TCP | 0.0.0.0:3389 | 0.0.0.0:0 | LISTENING | 9012 |
| … | … | … | … | … |
In this filtered output:
Protocol: Protocol used by the connection (e.g., TCP).Local Address: Local IP address and port.Foreign Address: Remote IP address and port.State: Connection state (e.g., LISTENING).PID: Process ID of the application or service associated with the connection.
TRACERT
TRACERT is used to trace the route taken by packets across an IP network to a specific destination.
tracert <hostname or IP address>NSLOOKUP
NSLOOKUP is a command-line tool used for querying the Domain Name System (DNS) to obtain domain name or IP address mapping.
nslookup <hostname>getmac
To retrieve the MAC address of a device on a Windows system, you typically use the getmac command. Here’s how you can use it:
getmacarp
To retrieve the ARP (Address Resolution Protocol) table on a Windows system, you can use the arp -a command. This command displays the current ARP cache, which contains mappings of IP addresses to MAC addresses. Here’s how you can use it:
arp -aWhen you run this command in the Command Prompt, it will display the ARP table with the IP addresses and corresponding MAC addresses of devices on the local network.
 Linux Networking Commands
Linux Networking Commands
IP ADDR
IP ADDR is used to display or manipulate routing, network devices, interfaces, and tunnels.
ip addrIFCONFIG
IFCONFIG is used to configure and display network interface parameters on Linux systems.
ifconfigPING
PING in Linux functions similarly to Windows. It is used to test network connectivity.
ping <hostname or IP address>NETSTAT
NETSTAT in Linux provides information about active network connections, routing tables, interface statistics, masquerade connections, and multicast memberships.
netstatnetstatRead more about lsof command
sudo lsof -i -P -n | grep LISTENLSOF - LIST OPEN FILES COMMAND
In Linux, the lsof command (short for “list open files”) is used to list information about files that are open by processes. When combined with specific options, it can also provide information about network connections.
The command: sudo lsof -i -P -n | grep LISTEN
lists all open files (-i) that are network-related, including sockets and ports (-i), in a numeric format (-P), and with host names turned off (-n). The output is then filtered using grep LISTEN to only show the entries where the connection state is “LISTENING”.
Example output after filtering:
| COMMAND | PID | USER | FD | TYPE | DEVICE | SIZE/OFF | NODE | NAME |
|---|---|---|---|---|---|---|---|---|
| sshd | 1234 | root | 3u | IPv4 | 1234 | 0t0 | TCP | *:22 (LISTEN) |
| nginx | 5678 | www-data | 6u | IPv4 | 5678 | 0t0 | TCP | *:80 (LISTEN) |
| apache | 9012 | apache | 4u | IPv6 | 9012 | 0t0 | TCP | *:443 (LISTEN) |
| … | … | … | … | … | … | … | … | … |
In this table:
COMMAND: Process name or command associated with the open file.PID: Process ID of the application or service.USER: User associated with the process.FD: File descriptor associated with the file.TYPE: Type of file (e.g., IPv4, IPv6).DEVICE: Device number associated with the file.SIZE/OFF: Size or offset of the file.NODE: Node associated with the file.NAME: Name of the file.
This command is useful for identifying which processes are listening on network ports, such as SSH, web servers, or other network services.
TRACEROUTE
TRACEROUTE is used to display the route packets take to network host.
traceroute <hostname or IP address>DIG
DIG (Domain Information Groper) is a flexible tool for interrogating DNS name servers.
dig <hostname>SS
SS is used to investigate sockets.
ssSS -TUNLP
SS -TUNLP is used to display TCP, UDP, UNIX, and RAW sockets, along with the process listening or owning them.
ss -tunlpNetwork Troubleshooting Devices
- Network Cable Tester: This device is used to verify the integrity and connectivity of network cables. It typically consists of a main unit and remote units. The main unit sends signals through the cable, while the remote unit(s) receive and analyze the signals, indicating whether the cable is functioning correctly.

- Toner and Probe Kit: A toner and probe kit helps trace and locate cables within walls, ceilings, or floors. The toner generates a distinct tone that travels along the cable, while the probe is used to detect and pinpoint the location of the tone, helping to identify the specific cable being traced.

- Ethernet Cable Certifier: Ethernet cable certifiers are advanced testing devices used to certify the performance of Ethernet cables. They measure parameters such as attenuation, crosstalk, and impedance to ensure that the cable meets industry standards and can support the desired network speeds and protocols.

- Cable Qualification Tester: Similar to cable certifiers, cable qualification testers assess the performance of network cables. They provide a pass/fail indication based on predefined performance thresholds but may not offer the same level of detailed testing and certification as certifiers.

- Network Multimeter: A network multimeter combines the functionalities of a traditional electrical multimeter with network testing capabilities. It can measure electrical properties such as voltage, current, and resistance, as well as diagnose network connectivity issues such as cable faults and signal loss.

- Fiber Optic Tester (OTDR): Optical Time-Domain Reflectometers (OTDRs) are used to test and troubleshoot fiber optic cables. They emit light pulses into the fiber and measure the reflections to assess the quality of the fiber link, detect faults, and determine the distance to any anomalies or breaks in the cable.

Conclusion
There are many more commands and ways to troubleshoot networks. Understanding and mastering these networking commands can greatly enhance your ability to troubleshoot and manage network-related issues on both Windows and Linux systems. Whether you’re a system administrator, network engineer, or simply a curious user, familiarity with these commands is invaluable in maintaining a healthy and efficient network environment.